
Easter Eve Human Sacrifice Pray
Radio Stew Webb and Joel March 30, 2018
26 minutes
Easter Eve Human Sacrifice! Pray! Stew Webb from Truth Warriors on Vimeo.
…


Easter Eve Human Sacrifice Pray
Radio Stew Webb and Joel March 30, 2018
26 minutes
Easter Eve Human Sacrifice! Pray! Stew Webb from Truth Warriors on Vimeo.
…

DOJ Official Bruce Ohr Hid Wife’s Fusion GPS Payments From Ethics Official
Bruce Ohr,
…

Larry Mizel Wide Open West Financial Cyber Attacks against Stew Webb Whistle blower
By Stew Webb Federal Whistle blower who has exposed Larry Mizel in violations of 18-USC-1010-1015.


 Was that the guy in the Whte House?
Was that the guy in the Whte House?
…

Former Marine Charged In Shooting, Hit-And-Run Of Controversial Seth Rich Investigator
A former Marine, who claims to have worked as a special agent with the Department of Energy, has been charged with shooting and running over Republican lobbyist Jack Burkman, who conducted a controversial investigation of former DNC staffer Seth Rich’s murder.
…

By: Sorcha Faal, and as reported to her Western Subscribers
Another ominous Security Council (SC) report circulating in the Kremlin today says that the “apologies being whispered into our ears” by Western diplomats who are expelling Russian diplomats in mass over a poisoning charade in the UK that no evidence exists for,
…

James Comey to speak at town hall after memoir release
Former FBI Director James Comey will join CNN for a Town Hall next month – a week after his eagerly awaited memoir will hit bookshelves, the cable network announced on Wednesday.
The one-hour,
…

Minneapolis FBI agent charged with leaking classified information to reporter
A Minneapolis FBI agent who started his career with the agency as an intern in 2000 has been charged with leaking classified information to the news website the Intercept. The Intercept
A Minneapolis FBI agent who started his career with the agency as an intern in 2000 has been charged with leaking classified information to the news website The Intercept.
…

Omar Mateen shot, killed 49 inside Orlando nightclub in June 2016
By Mark Lehman – Reporter, Daniel Dahm – Digital Manager
Posted: 7:08 AM, March 26, 2018 Updated: 3:16 PM, March 26, 2018
ORLANDO, Fla. – Attorneys for Noor Salman called for a mistrial after they say new details from prosecutors reveal that Pulse gunman Omar Mateen’s father was an FBI source and is currently under a criminal investigation.
…

CIA Admit They Have Infiltrated Mainstream Media in America
Declassified documents on the CIA website show that the intelligence agency has infiltrated every major news outlet in the America.
The documents state that a CIA task force “now has relationships with reporters from every major wire service,
…

FBI raids NXIVM President’s house as Raniere appears in Federal Court
Keith Raniere, the co-founder and leader of NXIVM, will remain in federal custody and be returned to New York later this week to face federal charges of sex trafficking and conspiracy to commit forced labor.
…


By Stew Webb Federal Whistle blower
A wake up call for all Christians about Israel
DNA GPS: What is the origin of Yiddish?
The origin of Yiddish, the millennium old language of Ashkenazic Jews, is something which linguists have questioned for decades.
…

By Stew Webb Federal Whistle blower
March 27, 2018
18-USC-4 Official Notice To President Trump
President Trump Stop NSA NAZI Espionage
http://www.stewwebb.com/2018/03/27/president-trump-stop-nsa-nazi-espionage/
President Trump Stop Cyber Terrorism against Stew Webb Whistle blower
The Computer Fraud and Abuse Act (CFAA) [18 U.S.C.
…

CRIMES AGAINST HUMANITY PSYCHOPATH JOHN BOLTON
CONSPIRATOR IN THE TREASONOUS THEFT
OF THE YEAR 2000 PRESIDENTIAL ELECTION
“WAR IS THE ANSWER” ….DEMANDS WWIII FOR ISRAEL….
HONORED AND REWARDED BY TRUMP! ! !
John Nichols: Bolton worked to stop Florida recount
By John Nichols
April 18,
…
 President Donald Trump
President Donald Trump
By Stew Webb Federal Whistle blower 34 years
March 27, 2018
President Trump Stop NSA NAZI Espionage
Updated April 21, 2018
Evidence of Cyber Attacks against Stew Webb Federal Whistleblower April 21 2018
http://www.stewwebb.com/2018/04/21/evidence-of-cyber-attacks-against-stew-webb-federal-whistleblower-april-21-2018/
Updated April 18 2018
Evidence of Cyber Attacks against Stew Webb Federal Whistle blower April 18 2018
Letter to Kansas City US Attorney Timothy Garrison purpose to Prosecute Cyber Terrorism
http://www.stewwebb.com/2018/04/18/letter-to-kansas-city-us-attorney-timothy-garrison-purpose-to-prosecute-cyber-terrorism/
Evidence of Cyber Attacks against Stew Webb Federal Whistleblower April 18 2018
http://www.stewwebb.com/2018/04/18/evidence-of-cyber-attacks-against-stew-webb-federal-whistleblower-april-18-2018/
President Trump Stop NSA NAZI Espionage
http://www.stewwebb.com/2018/03/27/president-trump-stop-nsa-nazi-espionage/
President Trump Stop Cyber Terrorism against Stew Webb Whistle blower
http://www.stewwebb.com/2017/12/07/president-trump-stop-cyber-terrorism-against-stew-webb-whistle-blower/
US CIA Cyber attacks against Stew Webb Whistle blower February 1,
…

By Stew Webb Federal Whistle blower 34 years
President Trump Stop Cyber Terrorism against Stew Webb Whistle blower
The Computer Fraud and Abuse Act (CFAA) [18 U.S.C. Section 1030] makes it illegal for anyone to distribute computer code or place it in the stream of commerce if they intend to cause either damage or economic loss.
…

By Stew Webb Federal Whistle blower
President Trump Stop Cyber Terrorism against Stew Webb Whistle blower
The Computer Fraud and Abuse Act (CFAA) [18 U.S.C. Section 1030] makes it illegal for anyone to distribute computer code or place it in the stream of commerce if they intend to cause either damage or economic loss.
…

By Stew Webb Federal Whistle blower 34 years
President Trump Stop Cyber Terrorism against Stew Webb Whistle blower
The Computer Fraud and Abuse Act (CFAA) [18 U.S.C. Section 1030] makes it illegal for anyone to distribute computer code or place it in the stream of commerce if they intend to cause either damage or economic loss.
…
By Stew Webb Federal Whistle blower
President Trump Stop Cyber Terrorism against Stew Webb Whistle blower
The Computer Fraud and Abuse Act (CFAA) [18 U.S.C. Section 1030] makes it illegal for anyone to distribute computer code or place it in the stream of commerce if they intend to cause either damage or economic loss.
…

Wide Open West Finance, LLC
By Stew Webb Federal Whistleblower 34 years
President Trump Stop Cyber Terrorism against Stew Webb Whistle blower
The Computer Fraud and Abuse Act (CFAA) [18 U.S.C. Section 1030] makes it illegal for anyone to distribute computer code or place it in the stream of commerce if they intend to cause either damage or economic loss.
…

By Stew Webb Federal Whistle blower
President Trump Stop Cyber Terrorism against Stew Webb Whistle blower
The Computer Fraud and Abuse Act (CFAA) [18 U.S.C. Section 1030] makes it illegal for anyone to distribute computer code or place it in the stream of commerce if they intend to cause either damage or economic loss.
…
Senior Executive Service (SES) IS the Deep State!
Senior Executive Service (SES) IS the Deep State! from Truth Warriors on Vimeo.
Your kind Contributions are very much appreciated thank you.
…
By Stew Webb Federal Whistle blower 34 years and still breathing.
Hillary Clinton Breaking News,
Hillary Thinks Women Can’t See She’s a Criminal! from Truth Warriors on Vimeo.
Your kind Contributions are very much appreciated thank you.
…

By Stew Webb Federal Whistle blower
This firing of a real scumbag Andrew McCabe from FBI Division number 5 the criminals at the FBI who attack Patriotic Americans, Federal Whistle blowers and anyone speaking truth about US Government corruption you will now go to Jail.
…

By Stew Webb Federal Whistle blower
President Trump Stop Cyber Terrorism against Stew Webb Whistle blower
The Computer Fraud and Abuse Act (CFAA) [18 U.S.C. Section 1030] makes it illegal for anyone to distribute computer code or place it in the stream of commerce if they intend to cause either damage or economic loss.
…

By Stew Webb Federal Whistle blower
President Trump Stop Cyber Terrorism against Stew Webb Whistle blower
The Computer Fraud and Abuse Act (CFAA) [18 U.S.C. Section 1030] makes it illegal for anyone to distribute computer code or place it in the stream of commerce if they intend to cause either damage or economic loss.
…

By Stew Webb Federal Whistle blower
President Trump Stop Cyber Terrorism against Stew Webb Whistle blower
The Computer Fraud and Abuse Act (CFAA) [18 U.S.C. Section 1030] makes it illegal for anyone to distribute computer code or place it in the stream of commerce if they intend to cause either damage or economic loss.
…
 Tim Timrawi
Tim Timrawi
By Stew Webb Federal Whistle blower
President Trump Stop Cyber Terrorism against Stew Webb Whistle blower
The Computer Fraud and Abuse Act (CFAA) [18 U.S.C. Section 1030] makes it illegal for anyone to distribute computer code or place it in the stream of commerce if they intend to cause either damage or economic loss.
…
By Stew Webb Federal Whistle blower 34 years
Letter to President Trump 2017-02-23 from Whistle blowers
http://www.stewwebb.com/2017/08/28/letter-to-president-trump-2017-02-23-from-whistle-blowers/
President Trump Stop Cyber Terrorism against Stew Webb Whistle blower
The Computer Fraud and Abuse Act (CFAA) [18 U.S.C.
…
By Stew Webb Federal Whistle blower
816-492-9809
federalwhistleblower@gmail.com
The Justice Department announced there new FOIA website.
Welcome to the first iteration of the new FOIA.gov. We’ll continue to improve upon this site in the future and look forward to your input.
…
785-213-0160
12820 SW K-4 HWY #B
Topeka, Kansas 66610-9749
federalwhistleblower@gmail.com
http://www.stewwebb.com/contact/
I Stew Webb have contributed to the following Books
http://www.stewwebb.com/books/
Current Radio Programs
http://www.stewwebb.com/stew-webb-radio-4-2/
Charlene Renee More Breaking News 2100 Show


“NEW”
Stew Webb Whistle blower Chronicles Video

October 25, 2010 Attempted murder of Stew Webb by 2 goons working for FBI JTFG Joint Task Force Group Kansas City, Missouri, Click on the picture to see additional information and pictures.

I am on social security disability because of 3 car crashes, 2 were attempted murder of me.
Click on the picture below and read the Private Investigators report Grandview, Missouri Police covered up for the FBI with a false report. This broke every vertebra in my neck.–Stew Webb
Attempted Murder of Stew Webb
Grandview, Missouri Police Obstruct Justice and tried to Cover up the car crash by FBI Stooges and Killers.
SEE: PROOF (Exhibits 1-22)
Stew Webb December 3, 2023 my story how I became a US Whistle blower
Copy and Paste the like below in your browser:

StewWebb-USMC-1971

Chatty Gargoyle at Denver International Airport
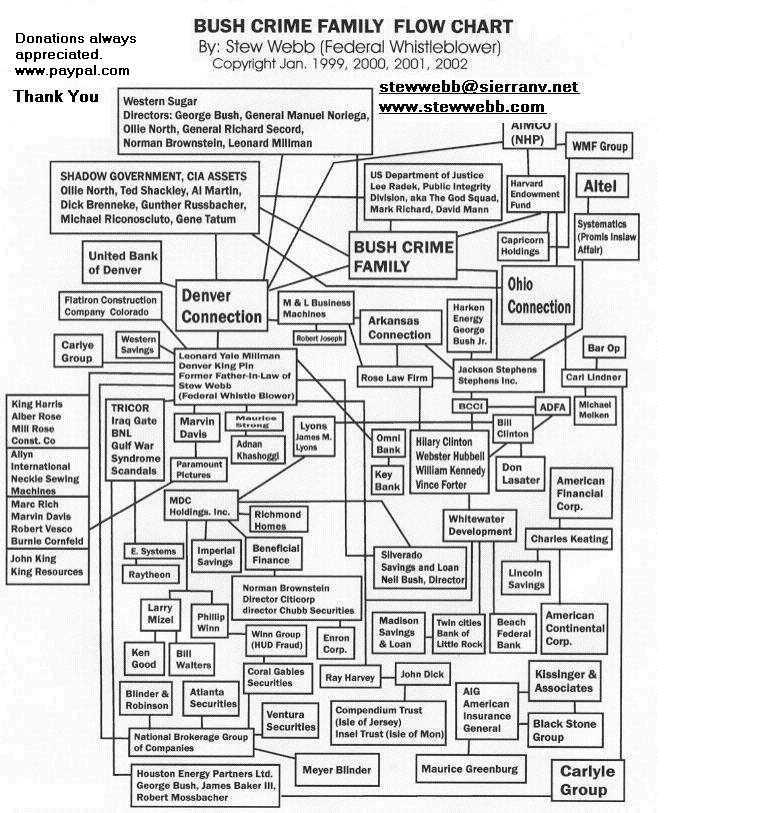
Larry Mizel and the Pro Jewish Mafia