By Stew Webb Federal Whistle blower
President Trump Stop Cyber Terrorism against Stew Webb Whistle blower
The Computer Fraud and Abuse Act (CFAA) [18 U.S.C. Section 1030] makes it illegal for anyone to distribute computer code or place it in the stream of commerce if they intend to cause either damage or economic loss. The CFAA focuses on a code’s damage to computer systems and the attendant economic losses, and it provides criminal penalties for either knowingly or recklessly releasing a computer virus into computers used in interstate commerce.
Someone convicted under the CFAA could face a prison sentence as long as 20 years and a fine of up to $250,000.
I will be posting the entire report proving over 6 million felonies over three years against my email account, my internet service providers and my website stewwebb.com under The Computer Fraud and Abuse Act (CFAA) [18 U.S.C. Section 1030] and Violations of my 1st Amendment Right to freedom of speech and Violations under RICO The Racketeering Influence and Corruption Organization Act plus attempted murders since 2009 because of filings in US District Court in Kansas City for Injunctive Relief from attempted murder using Blackwater Helicopter to lazer and kill this whistle blower then three car crashes from October 2010 – November 2011 which I have not been paid and which the car crashes has disabled this Whistle blower and I am being cheated out of one half of the social security minimum that I am entitled to under US law.
Related
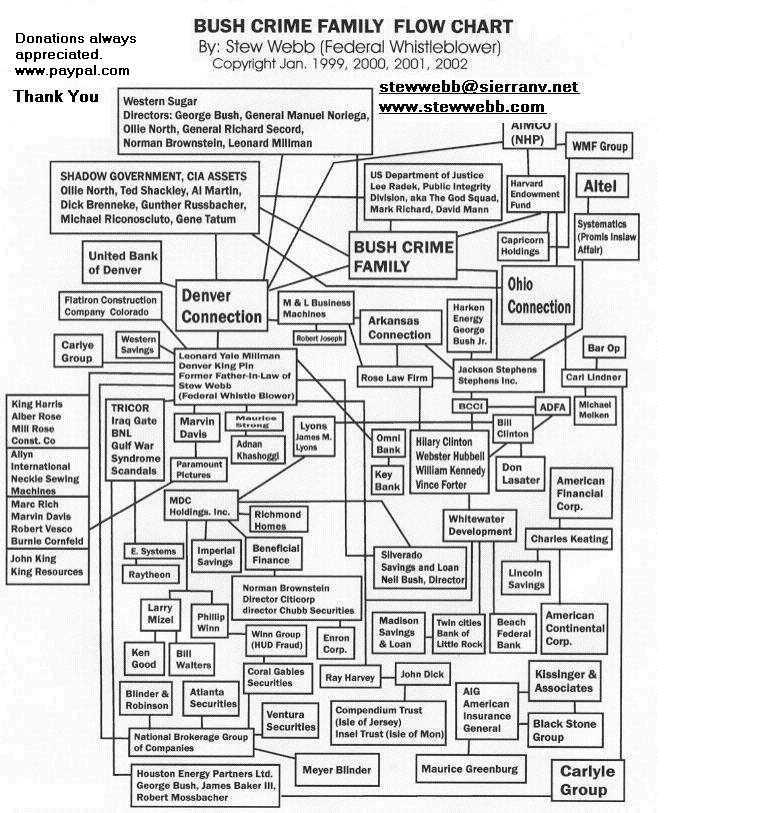
Below are at least 12 or more links to Israel, US DOD, British Intel, Larry Mizel, George HW Bush, Kansas City FBI, Missouri Fusing Center and many others in the US Shadow Government also now being called the Deep State. The Shadow Government is the top of the deep state also known as the Illuminati also known and the Council of 13 also known as the 12 Disciples of Satan, George HW Bush, Larry Mizel, Henry Kissinger, William Grace, Answar Ben Shari, Pope Benidick, David Rockefeller, Patrick WU aka Patrick WY, Meyer Rothchild, Paul Warberg, and I am missing 2 of the 12.
Evidence
Melbourne Australia SYNERGY WHOLESALE cyber attacks against Stew Webb Whistle blower
Melbourne, Australia visited http://www.stewwebb.com/
2/13/2018 8:05:24 AM (13 minutes ago)
IP: 103.252.152.3 Hostname: syd01.installatron.com
Browser: undefined
Mozilla/5.0 AppleWebKit/536.30.1 (KHTML, like Gecko) Version/6.0.5 Safari/536.30.1 Installatron (Mimicking WebKit)
@@@@@@@@@@@@@@@@@@@@@@@@
Scan wordfence Feb 8, 2018
File appears to be malicious: wp-content/deleteme.da2e7232dcfb448fb7e852be8d960503.php
Type: File
Issue Found 2018/02/08 6:23 pm
Critical
Ignore
Details
Filename: wp-content/deleteme.da2e7232dcfb448fb7e852be8d960503.php
File Type: Not a core, theme or plugin file.
Details: This file appears to be installed by a hacker to perform malicious activity. If you know about this file you can choose to ignore it to exclude it from future scans. The text we found in this file that matches a known malicious file is: “eval(base64_decode(“. The infection type is: Suspicious eval with a base64_decode.
Success deleting file
The file wp-content/deleteme.da2e7232dcfb448fb7e852be8d960503.php was successfully deleted.
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Eden Prairie, United States visited http://www.stewwebb.com/ deleteme.wppqbb.php
2/11/2018 10:12:42 PM (7 minutes ago)
IP: 206.191.194.1 Hostname: web1.sierranv.net
Browser: Firefox version 0.0 running on Win7
Mozilla/5.0 (Windows NT 6.1; WOW64; rv:17.0) Gecko/20100101 Firefox/17.0
@@@@@@@@@@@@@@@@@@@@
Topic Tag: deleteme « WordPress.org Forums
DeleteMe malicious file should I remove it? Started by: heroz. 2; 1; 1 year, 5 months ago · Steve Stern · WordPress file added deleteme.wp#######.php. Started by: wrowlands. 2; 1; 2 years, 9 months ago · dwinden · Log in from user ” deleteme”. Started by: veggiesdontbite. 2; 2; 2 years, 10 months ago · veggiesdontbite.
https://wordpress.org/support/topic-tag/deleteme/
Topic
Voices
Replies
Last Post
DeleteMe malicious file should I remove it?
Started by: heroz
2
1
1 year, 5 months ago
Steve Stern
WordPress file added deleteme.wp#######.php
Started by: wrowlands
2
1
2 years, 9 months ago
dwinden
Log in from user “deleteme”
Started by: veggiesdontbite
2
2
2 years, 11 months ago
veggiesdontbite
http://www.example.com/wp-content/deleteme
Started by: connectit
2
1
2 years, 11 months ago
Michael
What is this deleteme file and should I delete it?
Started by: skubeedoo
4
6
2 years, 8 months ago
marialulis
connectit
(@connectit)
2 years, 11 months ago
I was editing my footer in wordpress and edited the footer.php and functions.php and after updating the page I could no longer get access to my login and every time I go to log in it comes up with this: “http://www.example.com/wp-content/deleteme” with a long list of numbers and letters at the end.
I know exactly what I added to the functions.php and know I just need to delete that, however I can’t get into my wordpress to do so. All I get is a white blank screen.
How do I go about accessing this .php? Is there anyway it can edited in files -> file manager?
@@@@@@@@@@
Michael
(@alchymyth)
2 years, 11 months ago
review http://codex.wordpress.org/FTP_Clients
you will need to use FTP to access the files, or for example to rename the folder of your currently used theme, which should activate the default theme and allow you back into the dashboard to edit your files.
you will then need to change the folder name to its original, and re-activate your theme.
@@@@@@@@@@@@@@@@@
DeleteMe malicious file should I remove it?
heroz
(@heroz)
1 year, 5 months ago
I got this error message when I ran wordfence:
This file may contain malicious executable code: …/wp-content/deleteme.########################.php
What is this file and what action should I take?
>>>Image<<
Steve Stern
(@sterndata)
Guardian of the Interwebs
1 year, 5 months ago
Delete it, but understand that deleting it does not mean your system is clean. It got there somehow.
You need to start working your way through these resources:
https://codex.wordpress.org/FAQ_My_site_was_hacked
https://wordpress.org/support/topic/268083#post-1065779
Additional Resources:
http://sitecheck.sucuri.net/scanner/
http://www.unmaskparasites.com/
@@@@@@@@@@@@@@@@@@@@@@@@@@@
Steve Stern
(@sterndata)
Guardian of the Interwebs
1 year, 5 months ago
Delete it, but understand that deleting it does not mean your system is clean. It got there somehow.
You need to start working your way through these resources:
https://codex.wordpress.org/FAQ_My_site_was_hacked
https://wordpress.org/support/topic/268083#post-1065779
Additional Resources:
http://sitecheck.sucuri.net/scanner/
http://www.unmaskparasites.com/
dwinden
(@dwinden)
2 years, 9 months ago
A google search on deleteme.xxxx.php returned quite some info.
The files are created by a piece of software named Installatron that looks to be a tool offered by hosting providers who have ‘one click’ installations of software, like wordpress, joomla , etc
Anyway this is not an iTSec plugin issue.
dwinden
skubeedoo
(@skubeedoo)
3 years, 5 months ago
I got this error message when I ran wordfence:
This file may contain malicious executable code: …/wp-content/deleteme.########################.php
What is this file and what action should I take?
Wordfence Security – Firewall, Malware Scan, and Login Security
WFSupport
(@wfsupport)
3 years, 5 months ago
Hi
Great question! Thanks for asking. I found several references online to those files being created by Installatron that looks to be a tool offered by hosting providers who have ‘one click’ installations of software, like wordpress, joomla , etc. Does your hosting provider use that software? Check your control panel and let us know. You could send me a zipped copy of that file to tim [at] wordfence.com and I could take a look and see whats in it and offer an opinion.
Thanks!
tim
I hope WFSupport is still around so you can help me out. Or anyone.
My site is: http://www.ellaletraduce.co
I have made a number of mistakes (newbie with all of this) and I ended up uninstalling and deleting wordpress and installing it again.
I have a godaddy account and yes, through cPanel I am able to do the one-click installation with Installatron.
After installing it, I should be able to enter my WordPress dashboard, but when I go to wp-admin it redirects to http://www.ellaletraduce.co/wp-content/deleteme. and a bunch of numbers.
Also, when I try to go to wp-login.php it never loads and Firefox then shows me the message that “the connection has timed out”.
I would really appreciate it if you could help me out in any way.
@@@@@@@@@@@@@@@@@@@@@@@@@
Melbourne, Australia visited http://www.stewwebb.com/
2/13/2018 8:05:24 AM (13 minutes ago)
IP: 103.252.152.3 Hostname: syd01.installatron.com
Browser: undefined
Mozilla/5.0 AppleWebKit/536.30.1 (KHTML, like Gecko) Version/6.0.5 Safari/536.30.1 Installatron (Mimicking WebKit)
% Information related to ‘103.252.152.0 – 103.252.155.255’
[1024 addresses in this network]
% Abuse contact for ‘103.252.152.0 – 103.252.155.255’ is ‘noc@synergywholesale.com’
[1024 addresses in this network]
inetnum: 103.252.152.0 – 103.252.155.255
[1024 addresses in this network]
netname: SYNERGYWHOLESALE-AP
descr: SYNERGY WHOLESALE PTY LTD
descr: Suite 105
descr: 66 Victor Crescent
descr: Narre Warren VIC 3805
country: AU
org: ORG-SWPL1-AP
admin-c: SWN3-AP
tech-c: SWN3-AP
mnt-by: APNIC-HM
mnt-lower: MAINT-AU-SYNERGYWHOLESALE
mnt-routes: MAINT-AU-SYNERGYWHOLESALE
mnt-irt: IRT-SYNERGYWHOLESALE-AU
status: ALLOCATED PORTABLE
remarks: ——————————————————–
remarks: To report network abuse, please contact mnt-irt
remarks: For troubleshooting, please contact tech-c and admin-c
remarks: Report invalid contact via www.apnic.net/invalidcontact
remarks: ——————————————————–
last-modified: 2017-08-29T23:03:48Z
source: APNIC
irt: IRT-SYNERGYWHOLESALE-AU
address: PO Box 119
address: Beaconsfield VIC 3807
address: Australia
e-mail: noc@synergywholesale.com
abuse-mailbox: noc@synergywholesale.com
admin-c: SWN3-AP
tech-c: SWN3-AP
auth: # Filtered
mnt-by: MAINT-AU-SYNERGYWHOLESALE
last-modified: 2013-10-17T01:49:54Z
source: APNIC
organisation: ORG-SWPL1-AP
org-name: SYNERGY WHOLESALE PTY LTD
country: AU
address: Suite 105
address: 66 Victor Crescent
phone: +61 3 9013 8464
fax-no: +61 3 8080 6481
e-mail: noc@synergywholesale.com
mnt-ref: APNIC-HM
mnt-by: APNIC-HM
last-modified: 2017-08-20T22:54:24Z
source: APNIC
person: Synergy Wholesale NOC
address: PO BOX 119
Beaconsfield VIC 3807
country: AU
phone: +61.390138464
fax-no: +61.380806481
e-mail: noc@synergywholesale.com
nic-hdl: SWN3-AP
notify: noc@synergywholesale.com
abuse-mailbox: abuse@synergywholesale.com
mnt-by: MAINT-AU-SYNERGYWHOLESALE
last-modified: 2016-08-05T03:30:38Z
synergywholesale.com
Type: Bot
@@@@@@@@@@@@@@@@@@
Australia Melbourne, Australia visited http://www.stewwebb.com/
2/13/2018 8:05:24 AM (16 minutes ago)
IP: 103.252.152.3 Hostname: syd01.installatron.com
Browser: undefined
Mozilla/5.0 AppleWebKit/536.30.1 (KHTML, like Gecko) Version/6.0.5 Safari/536.30.1 Installatron (Mimicking WebKit)
Type: Bot
@@@@@@@@@@@@@@
Hacker Post
and info above delete me code
left off
installatron
Melbourne, Australia visited http://www.stewwebb.com/
2/13/2018 8:05:24 AM (13 minutes ago)
IP: 103.252.152.3 Hostname: syd01.installatron.com
Browser: undefined
Mozilla/5.0 AppleWebKit/536.30.1 (KHTML, like Gecko) Version/6.0.5 Safari/536.30.1 Installatron (Mimicking WebKit)
% Information related to ‘103.252.152.0 – 103.252.155.255’
[1024 addresses in this network]
% Abuse contact for ‘103.252.152.0 – 103.252.155.255’ is ‘noc@synergywholesale.com’
[1024 addresses in this network]
inetnum: 103.252.152.0 – 103.252.155.255
[1024 addresses in this network]
netname: SYNERGYWHOLESALE-AP
descr: SYNERGY WHOLESALE PTY LTD
descr: Suite 105
descr: 66 Victor Crescent
descr: Narre Warren VIC 3805
country: AU
org: ORG-SWPL1-AP
admin-c: SWN3-AP
tech-c: SWN3-AP
mnt-by: APNIC-HM
mnt-lower: MAINT-AU-SYNERGYWHOLESALE
mnt-routes: MAINT-AU-SYNERGYWHOLESALE
mnt-irt: IRT-SYNERGYWHOLESALE-AU
status: ALLOCATED PORTABLE
remarks: ——————————————————–
remarks: To report network abuse, please contact mnt-irt
remarks: For troubleshooting, please contact tech-c and admin-c
remarks: Report invalid contact via www.apnic.net/invalidcontact
remarks: ——————————————————–
last-modified: 2017-08-29T23:03:48Z
source: APNIC
irt: IRT-SYNERGYWHOLESALE-AU
address: PO Box 119
address: Beaconsfield VIC 3807
address: Australia
e-mail: noc@synergywholesale.com
abuse-mailbox: noc@synergywholesale.com
admin-c: SWN3-AP
tech-c: SWN3-AP
auth: # Filtered
mnt-by: MAINT-AU-SYNERGYWHOLESALE
last-modified: 2013-10-17T01:49:54Z
source: APNIC
organisation: ORG-SWPL1-AP
org-name: SYNERGY WHOLESALE PTY LTD
country: AU
address: Suite 105
address: 66 Victor Crescent
phone: +61 3 9013 8464
fax-no: +61 3 8080 6481
e-mail: noc@synergywholesale.com
mnt-ref: APNIC-HM
mnt-by: APNIC-HM
last-modified: 2017-08-20T22:54:24Z
source: APNIC
person: Synergy Wholesale NOC
address: PO BOX 119
Beaconsfield VIC 3807
country: AU
phone: +61.390138464
fax-no: +61.380806481
e-mail: noc@synergywholesale.com
nic-hdl: SWN3-AP
notify: noc@synergywholesale.com
abuse-mailbox: abuse@synergywholesale.com
mnt-by: MAINT-AU-SYNERGYWHOLESALE
last-modified: 2016-08-05T03:30:38Z
synergywholesale.com
Type: Bot
@@@@@@@@@@@@@@@@@@
Australia Melbourne, Australia visited http://www.stewwebb.com/
2/13/2018 8:05:24 AM (16 minutes ago)
IP: 103.252.152.3 Hostname: syd01.installatron.com
Browser: undefined
Mozilla/5.0 AppleWebKit/536.30.1 (KHTML, like Gecko) Version/6.0.5 Safari/536.30.1 Installatron (Mimicking WebKit)
Type: Bot
@@@@@@@@@@@
Stew Webb Site
United States Eden Prairie, United States visited http://www.stewwebb.com/
2/13/2018 8:05:00 AM (16 minutes ago)
IP: 206.191.194.1 Hostname: web1.sierranv.net
Browser: undefined
Installatron Plugin/9.1.36
Type: Bot
United States Eden Prairie, United States visited http://www.stewwebb.com/deleteme.wpixhf.php
2/13/2018 5:25:53 AM (2 hours 55 mins ago)
IP: 206.191.194.1 Hostname: web1.sierranv.net
Browser: Firefox version 0.0 running on Win7
Mozilla/5.0 (Windows NT 6.1; WOW64; rv:17.0) Gecko/20100101 Firefox/17.0
Type: 404 Not Found
United States Eden Prairie, United States visited http://www.stewwebb.com/deleteme.wp7hse.php
2/13/2018 5:25:49 AM (2 hours 55 mins ago)
IP: 206.191.194.1 Hostname: web1.sierranv.net
Browser: Firefox version 0.0 running on Win7
Mozilla/5.0 (Windows NT 6.1; WOW64; rv:17.0) Gecko/20100101 Firefox/17.0
Type: Bot
@@@@@@@@@@@@@@@@@@
Dallas, United States visited http://www.stewwebb.com/
2/13/2018 5:25:27 AM (3 hours 22 mins ago)
IP: 69.162.68.206 Hostname: dal01.installatron.com
Browser: undefined
Mozilla/5.0 AppleWebKit/536.30.1 (KHTML, like Gecko) Version/6.0.5 Safari/536.30.1 Installatron (Mimicking WebKit
Dallas, United States visited http://www.stewwebb.com/
2/13/2018 5:25:17 AM (3 hours 21 mins ago)
IP: 69.162.68.206 Hostname: dal01.installatron.com
Browser: undefined
Mozilla/5.0 AppleWebKit/536.30.1 (KHTML, like Gecko) Version/6.0.5 Safari/536.30.1 Installatron (Mimicking WebKit)
Sorry, but no data for that IP or domain was found.
P address 69.162.68.206
Reverse DNS (PTR record) dal01.installatron.com
DNS server (NS record) ns2.limestonenetworks.com (64.31.5.4)
ns1.limestonenetworks.com (64.31.5.3)
ASN number 46475
ASN name (ISP) Limestone Networks, Inc.
IP-range/subnet 69.162.64.0/18
69.162.64.0 – 69.162.127.255
Domains around 69.162.68.106
IP address #domains
69.162.68.3 1
69.162.68.18 1
69.162.68.50 5
69.162.68.58 1
69.162.68.62 1
69.162.68.98 1
69.162.68.106 245
Mail server Tools
mail.apelturismo.com.ar
mail.villa-pehuenia.com.ar
mail.plagaexpress.com
mail.dariolacheventos.com.ar
mail.matgauch.com
mail.begus.com.ar
mail.mgplot.com.ar
mail.estudioferullo.com
mail.anicellasgrutas.com.ar
mail.complejocaleu.com.ar
Name servers on 69.162.68.106
Overview of name servers hosted on this IP address. You can use the NS Neighbors tool to find domains using a name server.
Name server Tools
ns1.grupophi.com
tera1.teraserver.com.ar
ns1.eurowebdigital.com
ns2.eurowebdigital.com
ns1.nrgdns.net
dns1.tehagolaweb.com
69.162.68.107 1
69.162.68.118 20
69.162.68.156 1
69.162.68.162 4
69.162.68.166 1
69.162.68.178 1
69.162.68.198 20
69.162.68.210 2
69.162.68.215 1
69.162.68.219 1
69.162.68.226 2
69.162.68.227 1
69.162.68.228 1
69.162.68.229 1
69.162.68.230 2
69.162.68.234 1
69.162.68.236 1
69.162.68.250 1
NetRange: 69.162.64.0 – 69.162.127.255
CIDR: 69.162.64.0/18
Domains on 69.162.68.106
Domain Tools
titinas.com.ar
fmcarilo.com.ar
internetviedma.com.ar
emprenditel.com
import-arte.com.ar
santuariosanramon.org.ar
hierroyacero.com.ar
apelturismo.com.ar
flyfishingriopico.com.ar
lasgrutasrionegro.com.ar
NetName: LSN-DLLSTX-2
NetHandle: NET-69-162-64-0-1
Parent: NET69 (NET-69-0-0-0-0)
NetType: Direct Allocation
OriginAS: AS46475
Organization: Limestone Networks, Inc. (LIMES-2)
RegDate: 2008-06-27
Updated: 2012-02-24
OrgName: Limestone Networks, Inc.
OrgId: LIMES-2
Address: 400 S. Akard Street
Address: Suite 200
City: Dallas
StateProv: TX
PostalCode: 75202
Country: US
RegDate: 2007-12-04
Updated: 2017-01-28
NetRange: 69.162.64.0 – 69.162.127.255
CIDR: 69.162.64.0/18
214-242-3600
limestonenetworks.com
This domain is hosted by Limestone Networks, Inc. (AS46475). The first DNS server is ns3.limestonenetworks.com. The current IPv4 address is 64.31.5.5. The mail server with the highest priority is aspmx.l.google.com.
v=spf1 ip4:74.63.205.192/26 ip4:74.63.208.128/28 ip4:64.31.0.192/29
include:_spf.google.com ~al
DNS server (NS records) ns3.limestonenetworks.com (67.220.71.9)
ns1.limestonenetworks.com (64.31.5.3)
ns2.limestonenetworks.com (64.31.5.4)
Mail server (MX records) aspmx.l.google.com (173.194.76.27)
alt2.aspmx.l.google.com (74.125.130.26)
alt1.aspmx.l.google.com (64.233.163.27)
alt4.aspmx.l.google.com (64.233.160.27)
alt3.aspmx.l.google.com (74.125.204.26)
mx1.limestonenetworks.com (64.31.0.195)
mx2.limestonenetworks.com (74.63.205.207)
IP address (IPv4) 64.31.5.5
IP address (IPv6)
ASN number 46475
ASN name (ISP) Limestone Networks, Inc.
IP-range/subnet 64.31.0.0/18
64.31.0.0 – 64.31.63.255
Domain Name: LIMESTONENETWORKS.COM
Registrar URL: http://www.godaddy.com
Registrant Name: ******** ********
Registrant Organization: Limestone Networks, Inc.
Name Server: NS1.LIMESTONENETWORKS.COM
Name Server: NS2.LIMESTONENETWORKS.COM
DNSSEC: unsigned
@@@@@@@@@@@@
United States Eden Prairie, United States visited http://www.stewwebb.com/
2/13/2018 5:25:14 AM (3 hours 21 mins ago)
IP: 206.191.194.1 Hostname: web1.sierranv.net
Browser: undefined
Installatron Plugin/9.1.36
Eden Prairie, United States visited http://www.stewwebb.com/deleteme.wp7hse.php
2/13/2018 5:25:49 AM (3 hours 25 mins ago)
IP: 206.191.194.1 Hostname: web1.sierranv.net
Eden Prairie, United States visited http://www.stewwebb.com/deleteme.wpixhf.php
2/13/2018 5:25:53 AM (3 hours 26 mins ago)
IP: 206.191.194.1 Hostname: web1.sierranv.net
Eden Prairie, United States visited http://www.stewwebb.com/
2/13/2018 8:05:00 AM (48 minutes ago)
IP: 206.191.194.1 Hostname: web1.sierranv.net
Browser: undefined
Installatron Plugin/9.1.36
@@@@@@@@@@@@@@@@@@@@@@@@@@
United States Dallas, United States visited http://www.stewwebb.com/
2/13/2018 8:05:04 AM (49 minutes ago)
IP: 69.162.68.206 Hostname: dal01.installatron.com
Browser: undefined
Mozilla/5.0 AppleWebKit/536.30.1 (KHTML, like Gecko) Version/6.0.5
Safari/536.30.1 Installatron (Mimicking WebKit)
Sorry, but no data for that IP or domain was found.
@@@@@@@@@@@@@@@@@@@@@@
Melbourne, Australia visited http://www.stewwebb.com/
2/13/2018 8:05:24 AM (53 minutes ago)
IP: 103.252.152.3 Hostname: syd01.installatron.com
Browser: undefined
Mozilla/5.0 AppleWebKit/536.30.1 (KHTML, like Gecko) Version/6.0.5 Safari/536.30.1 Installatron (Mimicking WebKit)
% Information related to ‘103.252.152.0 – 103.252.155.255’
[1024 addresses in this network]
% Abuse contact for ‘103.252.152.0 – 103.252.155.255’ is ‘noc@synergywholesale.com’
[1024 addresses in this network]
inetnum: 103.252.152.0 – 103.252.155.255
[1024 addresses in this network]
netname: SYNERGYWHOLESALE-AP
descr: SYNERGY WHOLESALE PTY LTD
descr: Suite 105
descr: 66 Victor Crescent
descr: Narre Warren VIC 3805
country: AU
org: ORG-SWPL1-AP
admin-c: SWN3-AP
tech-c: SWN3-AP
mnt-by: APNIC-HM
mnt-lower: MAINT-AU-SYNERGYWHOLESALE
mnt-routes: MAINT-AU-SYNERGYWHOLESALE
mnt-irt: IRT-SYNERGYWHOLESALE-AU
status: ALLOCATED PORTABLE
remarks: ——————————————————–
remarks: To report network abuse, please contact mnt-irt
remarks: For troubleshooting, please contact tech-c and admin-c
remarks: Report invalid contact via www.apnic.net/invalidcontact
remarks: ——————————————————–
last-modified: 2017-08-29T23:03:48Z
source: APNIC
irt: IRT-SYNERGYWHOLESALE-AU
address: PO Box 119
address: Beaconsfield VIC 3807
address: Australia
e-mail: noc@synergywholesale.com
abuse-mailbox: noc@synergywholesale.com
admin-c: SWN3-AP
tech-c: SWN3-AP
auth: # Filtered
mnt-by: MAINT-AU-SYNERGYWHOLESALE
last-modified: 2013-10-17T01:49:54Z
source: APNIC
organisation: ORG-SWPL1-AP
org-name: SYNERGY WHOLESALE PTY LTD
country: AU
address: Suite 105
address: 66 Victor Crescent
phone: +61 3 9013 8464
fax-no: +61 3 8080 6481
e-mail: noc@synergywholesale.com
mnt-ref: APNIC-HM
mnt-by: APNIC-HM
last-modified: 2017-08-20T22:54:24Z
source: APNIC
person: Synergy Wholesale NOC
address: PO BOX 119
Beaconsfield VIC 3807
country: AU
phone: +61.390138464
fax-no: +61.380806481
e-mail: noc@synergywholesale.com
nic-hdl: SWN3-AP
notify: noc@synergywholesale.com
abuse-mailbox: abuse@synergywholesale.com
mnt-by: MAINT-AU-SYNERGYWHOLESALE
last-modified: 2016-08-05T03:30:38Z
source: APNIC
synergywholesale.com
This domain is hosted by SYNERGY WHOLESALE PTY LTD (AS45638). The first DNS server is ns2.corp.ventraip.net.au. The current IPv4 address is 103.42.108.73. The mail server with the highest priority is mx1.hostedmail.net.au.
v=spf1 a mx
@@@@@@@@@@@@@@@@@
?????????????????????
include:spf.synergywholesale.com
Domain IPv4 address Ranking Alexa Pagerank
synergywholesale.cc
synergywholesale.cloud 112.140.180.152
synergywholesale.co.nz
synergywholesale.co.uk
synergywholesale.com 103.42.108.73 753,321 -1
synergywholesale.com.au 103.42.108.73
synergywholesale.domains 112.140.180.152 -1
synergywholesale.fail 112.140.180.152 -1
synergywholesale.hosting 112.140.180.152
synergywholesale.info
synergywholesale.lighting 50.63.202.54 -1
synergywholesale.me
synergywholesale.mobi
synergywholesale.net 103.42.108.73
synergywholesale.net.au 103.42.108.73
synergywholesale.org
synergywholesale.wtf 112.140.180.152 -1
synergywholesaleproperties.com 209.99.64.55
IPv4 routes
No IPv4 ranges found
IPv6 routes
No IPv6 ranges found
Providers
No providers found
@@@@@@@@@@@@@@@@@
????????????????
include:spf.ausregistry.net.au ~al
@@@@@@@@@@@@@@@@@@
DNS server (NS records) ns2.corp.ventraip.net.au (112.140.180.136)
ns3.corp.ventraip.net.au (50.116.13.233)
ns1.corp.ventraip.net.au (112.140.176.12)
Mail server (MX records) mx1.hostedmail.net.au (103.252.153.1)
mx2.hostedmail.net.au (103.252.153.2)
IP address (IPv4) 103.42.108.73
IP address (IPv6) 2400:b800:2:1::73
ASN number 45638
ASN name (ISP) SYNERGY WHOLESALE PTY LTD
IP-range/subnet 103.42.108.0/24
103.42.108.0 – 103.42.108.255
Domain Name: synergywholesale.com
Registry Domain ID: 1820536225_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.synergywholesale.com
Registry Registrant ID: Not Available From Registry
Registrant Name: Domain Hostmaster
Registrant Organization: Synergy Wholesale Pty Ltd
Registrant Street: PO Box 119
Registrant Street:
Registrant Street:
Registrant City: Beaconsfield
Registrant State/Province: VIC
Registrant Postal Code: 3807
Registrant Country: AU
61.383999483
61.86783945
@@@@@@@@@@@@@@@@@@@@@@@@@
File appears to be malicious: stewwebb_construction_co_2.html.docx
Type: File
Issue Found 2018/02/12 10:31 pm
Critical
Ignore
Details
Filename: stewwebb_construction_co_2.html.docx
File Type: Not a core, theme or plugin file.
Details: This file appears to be installed by a hacker to perform malicious activity. If you know about this file you can choose to ignore it to exclude it from future scans. The text we found in this file that matches a known malicious file is: “\Xbn”. The infection type is: Javascript code indicative of malware.
Need help with a hacked website?
Our team of security experts will clean the infection and remove malicious content. Once your site is restored we will provide a detailed report of our findings. Includes a 1-year Wordfence Premium license.
File appears to be malicious: wp-content/plugins/wordfence/models/block/wfBlock.php
Type: File
Issue Found 2018/02/12 10:31 pm
Critical
Ignore
Details
Filename: wp-content/plugins/wordfence/models/block/wfBlock.php
File Type: Not a core, theme or plugin file.
Details: This file appears to be installed by a hacker to perform malicious activity. If you know about this file you can choose to ignore it to exclude it from future scans. The text we found in this file that matches a known malicious file is: “\x00”. The infection type is: Javascript code indicative of malware.
File appears to be malicious: Appeal_20121212.htm.pdf
Type: File
Issue Found 2018/02/12 10:31 pm
Critical
Ignore
Details
Filename: Appeal_20121212.htm.pdf
File Type: Not a core, theme or plugin file.
Details: This file appears to be installed by a hacker to perform malicious activity. If you know about this file you can choose to ignore it to exclude it from future scans. The text we found in this file that matches a known malicious file is: “\XvC”. The infection type is: Javascript code indicative of malware.
File appears to be malicious: wp-content/plugins/wordfence/lib/wfGeoIP.php
Type: File
Issue Found 2018/02/12 10:31 pm
Critical
Ignore
Details
Filename: wp-content/plugins/wordfence/lib/wfGeoIP.php
File Type: Not a core, theme or plugin file.
Details: This file appears to be installed by a hacker to perform malicious activity. If you know about this file you can choose to ignore it to exclude it from future scans. The text we found in this file that matches a known malicious file is: “\xff”. The infection type is: Javascript code indicative of malware.
File appears to be malicious: wp-content/plugins/wordfence/lib/wordfenceURLHoover.php
Type: File
Issue Found 2018/02/12 10:31 pm
Critical
Ignore
Details
Filename: wp-content/plugins/wordfence/lib/wordfenceURLHoover.php
File Type: Not a core, theme or plugin file.
Details: This file appears to be installed by a hacker to perform malicious activity. If you know about this file you can choose to ignore it to exclude it from future scans. The text we found in this file that matches a known malicious file is: “\x00”. The infection type is: Javascript code indicative of malware.
File appears to be malicious: wp-content/plugins/wordfence/vendor/wordfence/wf-waf/src/lib/utils.php
Type: File
Issue Found 2018/02/12 10:31 pm
Critical
Ignore
Details
Filename: wp-content/plugins/wordfence/vendor/wordfence/wf-waf/src/lib/utils.php
File Type: Not a core, theme or plugin file.
Details: This file appears to be installed by a hacker to perform malicious activity. If you know about this file you can choose to ignore it to exclude it from future scans. The text we found in this file that matches a known malicious file is: “\x00”. The infection type is: Javascript code indicative of malware.
File appears to be malicious: wp-content/wflogs/rules.php
Type: File
Issue Found 2018/02/12 10:31 pm
Critical
Ignore
Details
Filename: wp-content/wflogs/rules.php
File Type: Not a core, theme or plugin file.
Details: This file appears to be installed by a hacker to perform malicious activity. If you know about this file you can choose to ignore it to exclude it from future scans. The text we found in this file that matches a known malicious file is: “\xC2”. The infection type is: Javascript code indicative of malware.
File appears to be malicious: wp-content/plugins/wordfence/js/date.1518460764.js
Type: File
Issue Found 2018/02/12 10:31 pm
Critical
Ignore
Details
Filename: wp-content/plugins/wordfence/js/date.1518460764.js
File Type: Not a core, theme or plugin file.
Details: This file appears to be installed by a hacker to perform malicious activity. If you know about this file you can choose to ignore it to exclude it from future scans. The text we found in this file that matches a known malicious file is: “\x27”. The infection type is: Javascript code indicative of malware.
File appears to be malicious: wp-content/plugins/wordfence/lib/wfUtils.php
Type: File
Issue Found 2018/02/12 10:31 pm
Critical
Ignore
Details
Filename: wp-content/plugins/wordfence/lib/wfUtils.php
File Type: Not a core, theme or plugin file.
Details: This file appears to be installed by a hacker to perform malicious activity. If you know about this file you can choose to ignore it to exclude it from future scans. The text we found in this file that matches a known malicious file is: “\x00”. The infection type is: Javascript code indicative of malware.
File appears to be malicious: wp-content/plugins/wordfence/js/admin.1518460764.js
Type: File
Issue Found 2018/02/12 10:31 pm
Critical
Ignore
Details
Filename: wp-content/plugins/wordfence/js/admin.1518460764.js
File Type: Not a core, theme or plugin file.
Details: This file appears to be installed by a hacker to perform malicious activity. If you know about this file you can choose to ignore it to exclude it from future scans. The text we found in this file that matches a known malicious file is: “\x00”. The infection type is: Javascript code indicative of malware.
@@@@@@@@@@@@@@@@@@@@@@
Alert generated at Monday 12th of February 2018 at 10:32:39 PM
Critical Problems:
* File appears to be malicious: wp-content/plugins/wordfence/models/block/wfBlock.php
* File appears to be malicious: Appeal_20121212.htm.pdf
* File appears to be malicious: wp-content/plugins/wordfence/lib/wfGeoIP.php
* File appears to be malicious: wp-content/plugins/wordfence/lib/wordfenceURLHoover.php
* File appears to be malicious: wp-content/plugins/wordfence/vendor/wordfence/wf-waf/src/lib/utils.php
* File appears to be malicious: wp-content/wflogs/rules.php
* File appears to be malicious: wp-content/plugins/wordfence/js/date.1518460764.js
* File appears to be malicious: wp-content/plugins/wordfence/lib/wfUtils.php
* File appears to be malicious: wp-content/plugins/wordfence/js/admin.1518460764.js
* File appears to be malicious: stewwebb_construction_co_2.html.docx
Your kind Contributions are very much appreciated thank you. – Stew Webb