
Scott Israel booster convicted in tax evasion, gun cases
By Bob Norman – Investigative Reporter
(See Video)
PEMBROKE PARK, Fla. – A political committee supporting Broward County Sheriff Scott Israel has raised $96,000 so far,
…

Scott Israel booster convicted in tax evasion, gun cases
By Bob Norman – Investigative Reporter
(See Video)
PEMBROKE PARK, Fla. – A political committee supporting Broward County Sheriff Scott Israel has raised $96,000 so far,
…

Broward County Sheriff Scott Israel,
…
Feb 19, 2018
Americans need to expose and fight the political criminals who are causing the violence against children.
“And I looked, and beheld a pale horse, and the one sitting on it, the name of him is Death,
…

By Stew Webb Federal Whistle blower
Roger Stone who claims LBJ murdered JFK, not true Daddy Bush killed JFK.
Stone is a regular on Israel’s stooge Alex Jones radio a disinformation mouth for Daddy Bush.
You be the Judge??
Among the sheriff’s hires: three associates of the notorious political trickster Roger Stone,…

By Stew Webb Federal Whistle blower
President Trump Stop Cyber Terrorism against Stew Webb Whistle blower
The Computer Fraud and Abuse Act (CFAA) [18 U.S.C. Section 1030] makes it illegal for anyone to distribute computer code or place it in the stream of commerce if they intend to cause either damage or economic loss.
…

By Stew Webb Federal Whistle blower
President Trump Stop Cyber Terrorism against Stew Webb Whistle blower
The Computer Fraud and Abuse Act (CFAA) [18 U.S.C. Section 1030] makes it illegal for anyone to distribute computer code or place it in the stream of commerce if they intend to cause either damage or economic loss.
…

By Stew Webb Federal Whistleblower
This school shooting smells like George HW Bush “Daddy Bush” behind it?
Question were is the story about yesterdays NSA attack and the three they caught?
Your kind Contributions are very much appreciated thank you.
…
By Stew Webb Federal Whistleblower
RIP Super Spook NSA – CIA Otis Johnson Stone-R to death July 2017 by George HW Bush and his E-Systems Weststar Satellite’s a Department of Defense Contractor based in Dallas, Texas.
Super Spook Otis Johnson Maritime activities against the USSR
In 1973,
…

By Stew Webb Federal Whistle blower
The Computer Fraud and Abuse Act (CFAA) [18 U.S.C. Section 1030] makes it illegal for anyone to distribute computer code or place it in the stream of commerce if they intend to cause either damage or economic loss.
…

U.S. CFTC to fine UBS, Deutsche Bank, HSBC for futures market spoofing, manipulation
January 26, 2018, 06:35:00 PM EDT By Reuters
WASHINGTON, Jan 26 (Reuters) – The U.S. derivatives regulator is set to announce it has fined European lenders UBS,
…
785-213-0160
12820 SW K-4 HWY #B
Topeka, Kansas 66610-9749
federalwhistleblower@gmail.com
http://www.stewwebb.com/contact/
I Stew Webb have contributed to the following Books
http://www.stewwebb.com/books/
Current Radio Programs
http://www.stewwebb.com/stew-webb-radio-4-2/
Charlene Renee More Breaking News 2100 Show
“NEW”
Stew Webb Whistle blower Chronicles Video
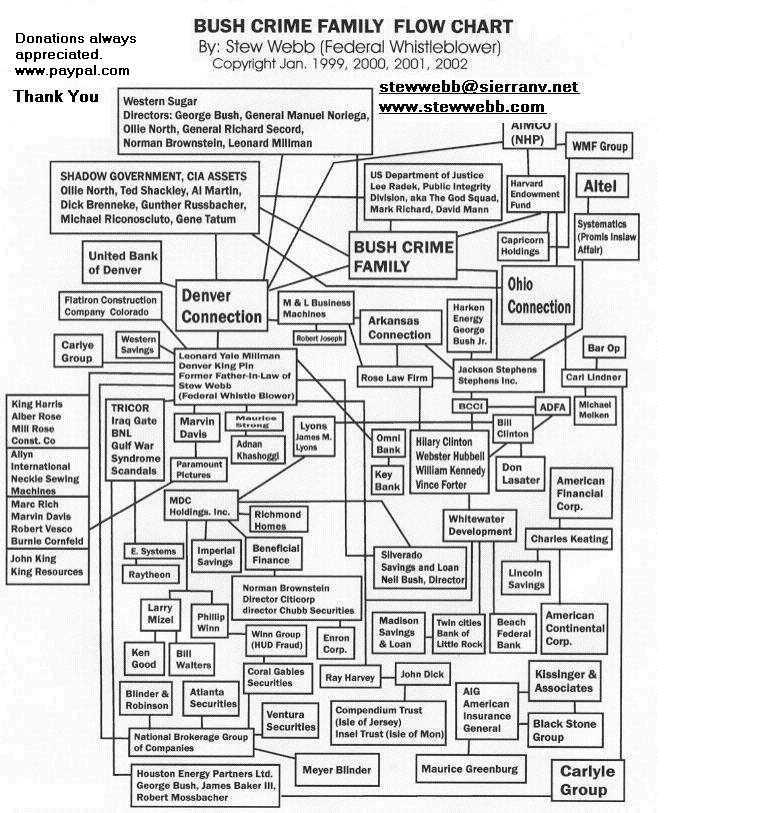

October 25, 2010 Attempted murder of Stew Webb by 2 goons working for FBI JTFG Joint Task Force Group Kansas City, Missouri, Click on the picture to see additional information and pictures.

I am on social security disability because of 3 car crashes, 2 were attempted murder of me.
Click on the picture below and read the Private Investigators report Grandview, Missouri Police covered up for the FBI with a false report. This broke every vertebra in my neck.–Stew Webb
Attempted Murder of Stew Webb
Grandview, Missouri Police Obstruct Justice and tried to Cover up the car crash by FBI Stooges and Killers.
SEE: PROOF (Exhibits 1-22)
Stew Webb December 3, 2023 my story how I became a US Whistle blower
Copy and Paste the like below in your browser:

StewWebb-USMC-1971

Chatty Gargoyle at Denver International Airport
Larry Mizel and the Pro Jewish Mafia